MOGADISHU, Somalia – 7 September, 2023 – The Somali Journalists Syndicate (SJS), in collaboration with Qurium, a nonprofit foundation, has revealed that the U.S. company RayoByte, along with its affiliate Sprious, controlled the infrastructure used for the Distributed Denial-of-Service Attack (DDoS) that temporarily shut down SJS’s online servers last month.
Thanks to the relentless support from Qurium and its digital defenders, the attack was successfully mitigated. However, a subsequent forensic investigation uncovered that in late August, the SJS website, www.sjs.ileysinc.com, was flooded by a massive DDoS attack originating from over 20,000 unique IP addresses.
While we recognize that SJS is not the sole news outlet targeted by DDoS attacks facilitated by RayoByte’s services, the timing of this cyberattack couldn’t have been worse. Days later, plain-clothed Somali intelligence officers kidnapped SJS Secretary of Information and Human Rights Mohamed Ibrahim Osman Bulbul due to his reporting on alleged police corruption, which was broadcasted by Kaab TV. These concurrent crises have put immense strain on our organization.
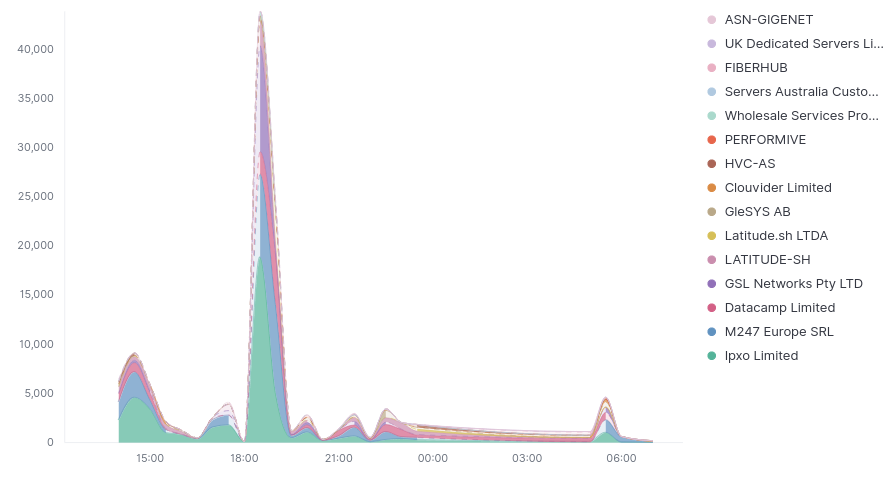
Qurium’s analysis indicates that it thwarted nearly 20,000 IP addresses coming to SJS website with millions of requests on August 18 and 19. Nearly 50% of this traffic was routed through RayoByte and its hosting partners, as per the analysis. The remaining traffic came through various other online channels, including virtual private networks (VPNs).
Throughout August, SJS received reports from several other media houses that experienced similar DDoS attacks, some lasting for days or weeks.
During the investigation of the DDoS attack traffic logs on SJS website, Qurium identified prefixes associated with OpenVPN/IKE rather than proxy services. Initially, attention was focused on six prefixes from AS206092/SECFIREWALLAS, revealing VPN services. These networks displayed certificates from three VPN products by Kape Technologies: privateinternetaccess, cyberghost, expressvpn. The evidence strongly suggested that VPN infrastructures were exploited in the DDoS attacks.
Qurium also identified IP addresses originating from ISPs such as GSL Networks Pty LTD, Latitude.sh LTDA, and SECFIREWALLAS, all categorized as “VPN Consumer Network” by ARIN.
Qurium promptly informed the three VPN providers, IPVanish, NordVPN, and ExpressVPN, that their infrastructures were involved in carrying out denial of service attacks.
RayoByte, headquartered in Lincoln, Nebraska, formerly known as Blazing SEO, is among the companies that offer clients access to Internet Protocol (IP) addresses for “scraping” data from websites, listing various prices based on variables like type and speed.
Sprious, the parent company of RayoByte, informed Qurium via email that they had “removed the abusive user” from their network.
However, the remaining VPN providers mentioned have yet to provide an explanation at the time of this report.
“While we are relieved that Qurium managed to mitigate this online attack, we cannot ignore the fact that unscrupulous groups are funded to rent or buy proxy IP addresses to carry out online attacks against vulnerable media and human rights organizations like SJS,” SJS Secretary-General, Abdalle Ahmed Mumin said. “The critical question now is, who has funded this substantial attack? Where is the funding coming from?”
“In the face of Somalia’s dire humanitarian crisis, it is disheartening that authorities in Mogadishu are financing criminals to launch online attacks against organizations like SJS. Will they ever be held accountable for this?” Mr. Mumin added.